-
Release Notes
- July 8, 2024
- May 22, 2024
- April 17, 2024
- March 20, 2024
- February 22, 2024
- January 18, 2024
- 2023 Releases
- 2022 Releases
-
2021 Releases
- December 20, 2021
- December 1, 2021
- November 22, 2021
- November 4, 2021
- October 26, 2021
- September 30, 2021
- September 22, 2021
- September 2, 2021
- August 16, 2021
- August 2, 2021
- July 19, 2021
- July 1, 2021
- June 17, 2021
- June 1, 2021
- April 30, 2021
- April 8, 2021
- March 25, 2021
- March 15, 2021
- February 25, 2021
- February 8, 2021
- January 28, 2021
- January 21, 2021
- January 13, 2021
- 2020 Releases
- Getting Started
- Ports
- Cross Connects
- Point-to-Point
- Virtual Circuits
- Cloud Connections
- Cloud Router
- Marketplace & IX
- Administration
- Billing
- Troubleshooting & FAQ
- Technical Reference
- Partners Portal
- API & Automation
April 6, 2023 Release Notes
New features
Cloud-side provisioning for Google Cloud connections
You can now add Google Cloud credentials to PacketFabric, allowing you to perform certain Google Cloud tasks from PacketFabric, including:
- Provisioning the Google Cloud VLAN attachment from the PacketFabric portal/API.
- Automatically deleting the associated VLAN attachment when deleting the connection from the PacketFabric.
- The ability to view VLAN attachment details from PacketFabric.
- The ability to modify VLAN attachment information from PacketFabric, including updating the MTU, both BGP ASNs, advertised prefixes, keepalive interval, and MD5 key.
When provisioning a Hosted connection or a Cloud Router connection to Google Cloud, you will now see an option to provision the cloud side of the connection:
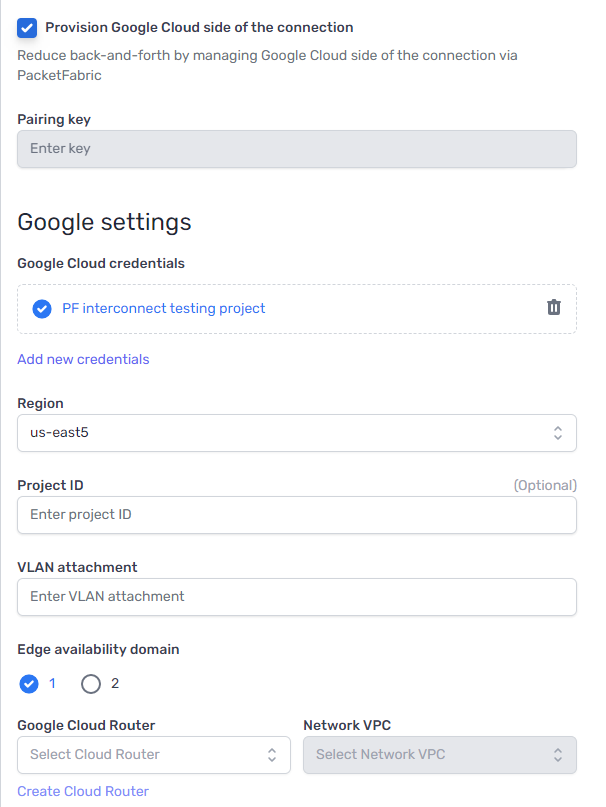
You will be asked to enter a Google Cloud key. Once added, you can provision and accept the Google VLAN attachment while building the PacketFabric connection.
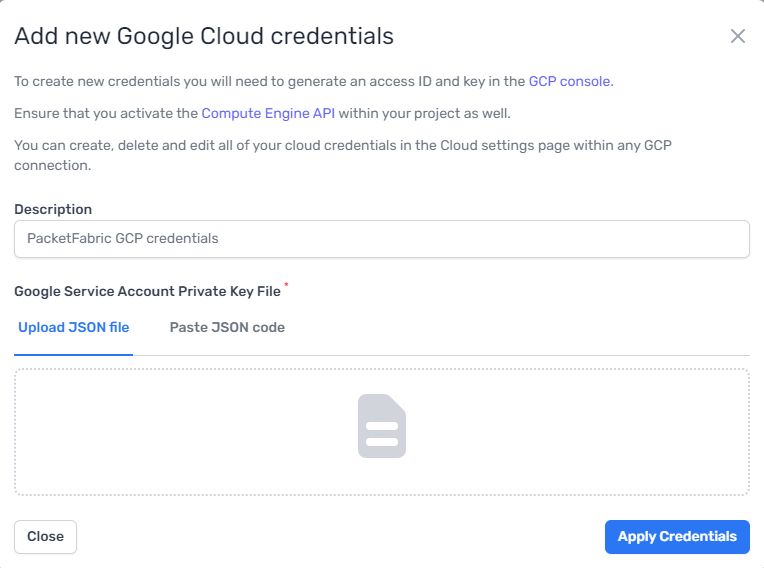
For more information, see Google Access Keys, Create a Hosted Connection to Google, and Add a Google Partner Interconnect to a Cloud Router.
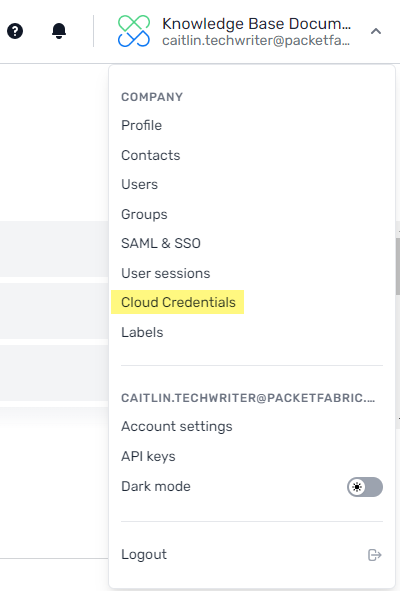
Cloud credentials management
A new Cloud Credentials page is available from the admin menu.
From here you can add and manage saved credentials to Google and AWS. For more information, see Cloud Credentials.
Changes and enhancements
Miscellaneous
- Cloud Router connections to dedicated cloud ports now show a cloud icon in the Cloud Router connections list.
- The Allow longer prefixes toggle in the BGP session settings for a Cloud Router connection has been replaced with a Match type selection. This was done to prevent user confusion and to reflect how this option appeared when setting it on a per-prefix basis.
- A link to the port details page was added to the details page of Cloud Router dedicated port connections.
Bug fixes
- Some Cloud Router connections were displaying the wrong POP ID for the on-ramp.
- The portal front end was allowing MD5 field submissions with invalid lengths.
Updated on 08 Feb 2024