Google Cloud Access Keys
Adding Google Cloud access keys to your PacketFabric environment allows you to perform certain Google Cloud tasks from PacketFabric, including:
- Provisioning the Google Cloud VLAN attachment from the PacketFabric portal/API.
- Automatically deleting the associated VLAN attachment when deleting the connection from PacketFabric.
- The ability to view VLAN attachment details from PacketFabric.
- The ability to modify VLAN attachment information from PacketFabric, including updating the MTU, both BGP ASNs, advertised prefixes, keepalive interval, and MD5 key.
This is an optional convenience and is not required to create or manage Google cloud connections.
NOTE: Only admins on your Google Cloud account have access to do this. You may need to request access, or request that an admin generate credentials on your behalf.
Once generated and added to your PacketFabric account, the credentials can be shared by all users in the PacketFabric portal. However, the specific access key remains hidden to prevent the credentials from being transferred elsewhere.
Enable the required APIs
- If you have not yet used a service account in your Google Cloud project, you may need to enable the service account API. See Create service accounts in the Google Cloud documentation.
- Enable the Compute Engine API (ensure you are in the correct project).
Create a custom role
-
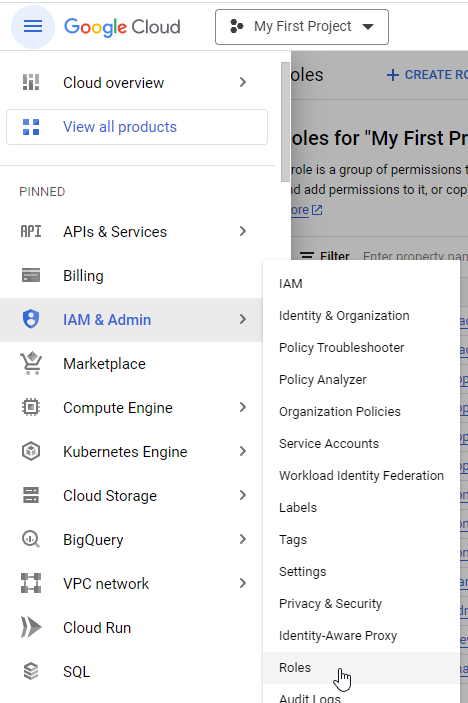
From the Google Cloud console, go to IAM & Admin > Roles.
-
Click Create role.
-
Complete the following fields:
- Header row
- Field
- Description
- Title
- Title
- Enter a name for the role that will make it easily identifiable, e.g. “Cloud interconnect management.”
- description
- Description
- Optionally, provide a description for the role.
- Service account ID
- ID
- Enter an ID that reflects the role name.
- Header row
-
Click Add permissions and then find and select the following permissions (18):
compute.networks.get
compute.networks.list
compute.networks.updatePolicy
compute.subnetworks.get
compute.subnetworks.list
compute.routers.create
compute.routers.delete
compute.routers.get
compute.routers.list
compute.routers.update
compute.interconnectAttachments.create
compute.interconnectAttachments.delete
compute.interconnectAttachments.get
compute.interconnectAttachments.list
compute.interconnectAttachments.update
compute.regionOperations.get
compute.regionOperations.list
compute.regions.list -
Click Create.
Create a service account
-
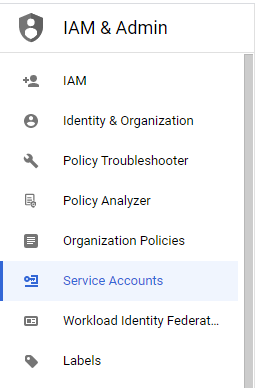
From the IAM & Admin pages, select Service Accounts.
-
Click Create service account and complete the following fields:
-
Header row
- Field
- Description
-
Service account name
- Service account name
- Enter a name for the service account that will appear in the console.
-
Service account ID
- Service account ID
- The account ID is generated from the service name.
-
description
- Description
- Optionally, provide a description for the service account.
-
-
Click Create and continue.
-
Select the custom role you created in the section above (Create a custom role).
-
Optionally, you can link the service account to a user or group. For more information, see Manage access to service accounts.
-
Click Done.
Generate a key
-
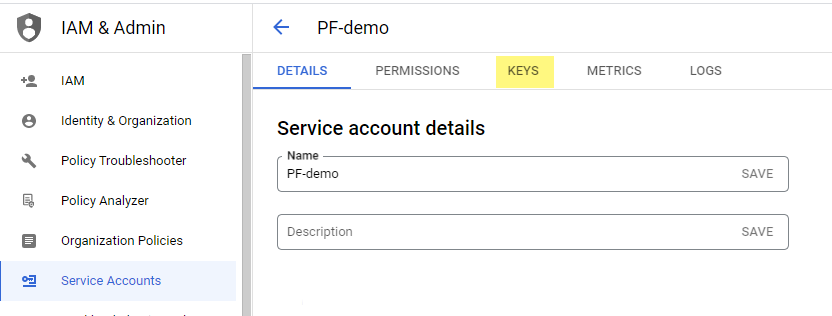
From the Service Accounts page in the Google Cloud console, click the name of the service account you just created to go to its details.
-
Select the Keys tab.
-
Select Add key > Create new key.
-
Select JSON and then click Create.
The private key is automatically downloaded. This is the only time you can download the key.
Add the key to PacketFabric
Note that cloud credentials are shared among users within the PacketFabric account. For example, one user can add the credentials when creating Connection 1, and then another user can reuse them when creating Connection 2.
You can add the key in several ways:
-
From Admin > Cloud Credentials. Click Add Google Credentials.
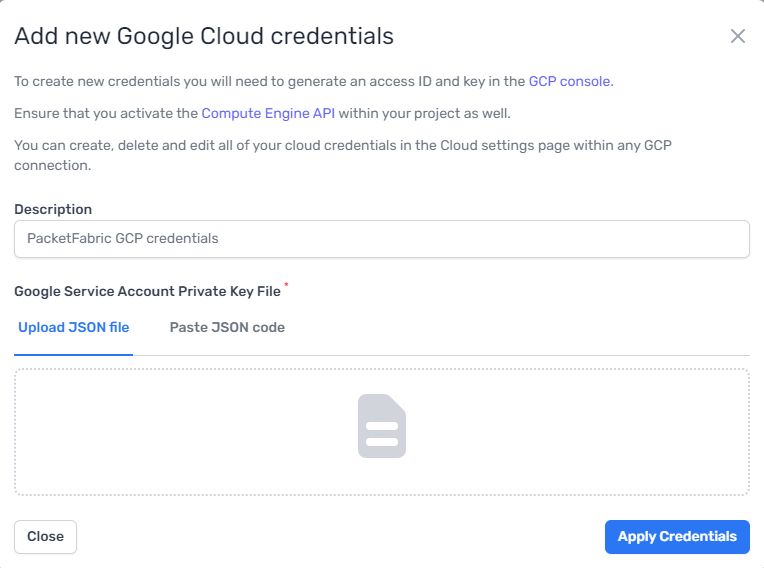
-
When you select Provision Google Cloud side of the connection when creating a connection, you have the option to add new credentials.
-
From the Cloud Settings tab on the details page of an existing connection.
If you provisioned the connection and skipped the Provision Google Cloud side of the connection option, you can still add a Google access key to the connection. This will allow you to view and modify VLAN attachment details from the portal.
Manage keys
You can manage credentials from the details page of a cloud connection under the Cloud Settings tab.
You can also manage keys from Admin > Cloud Credentials:
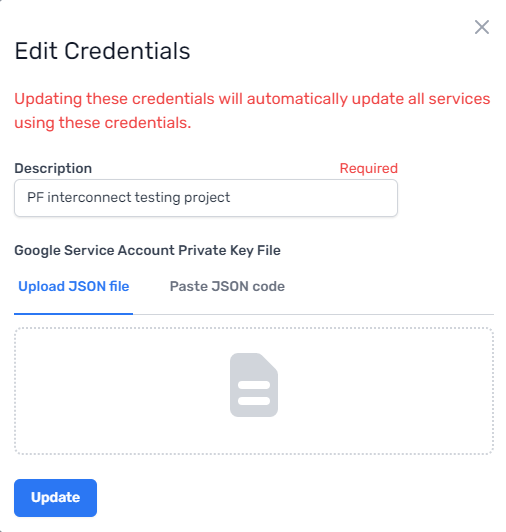
From here you can add, edit, and delete credentials. This might be necessary for credentials that are expired or have been compromised.
When editing credentials, you will be required to re-enter the JSON key.