Configure BGP for Port Connections
Before you begin, ensure you have completed the steps outlined in Add a Connection from a Port to the Cloud Router.
Manage BGP information for a Cloud Router connection
Go to the Cloud Routers page in the PacketFabric portal.
If you have not yet configured a BGP session, you will see the Configure BGP action from the Cloud Routers table:
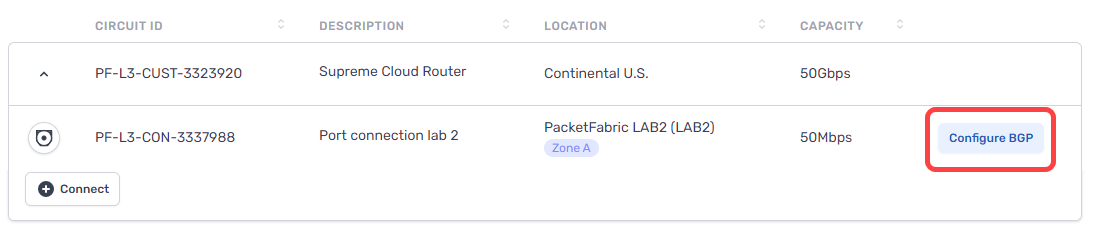
If you have configured the BGP session but wish to make changes, you can access the BGP settings from the BGP Sessions page or by clicking the connection to open its side panel.
From here, click Manage BGP or click the view icon under BGP Sessions:
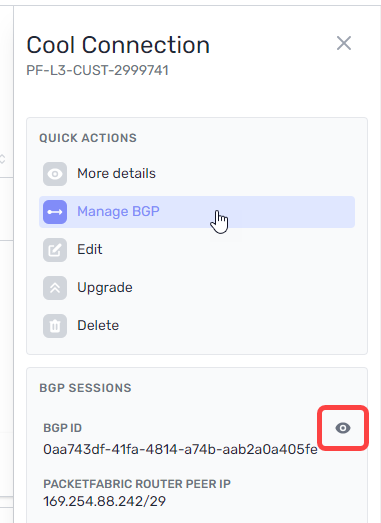
Complete the following fields and then click Submit.
BGP Settings
- Header row
- Field
- Description
- Row 1
- PacketFabric ASN
- This is the ASN you specified when creating your PacketFabric Cloud Router. You cannot edit this field.
- Row 1
- ASN
- This is the ASN for your on-premises environment. If you have one, you can use your public ASN. Otherwise, you can select a private ASN.
- Row 1
-
PacketFabric Router Peer IP + Mask (CIDR notation)
-
Enter an IP prefix of your choice.
If you provisioned the connection with a public IP address, this is pre-populated.
-
- Row 1
-
Customer On-premises Router Peer IP + Mask (CIDR notation)
-
Enter an IP address for the router connected to PacketFabric via cross connect.
If you provisioned the connection with a public IP address, this is pre-populated and cannot be edited.
-
- Row 1
- BGP Authentication Key
- Optionally, you can include an MD5 authentication key. Limited to 80 characters.
BFD settings
Select Enable BFD to enable Bidirectional Forwarding Detection (BFD) for this connection.
When BFD is enabled, test packets are periodically sent to BGP peers. If a peer fails to reply after a specified interval and number of attempts, the BGP session shuts down.
On its own, BGP will take about 90 seconds to detect a failure and shut down. With BFD, you can detect failures significantly faster.
- Row
- Field
- Description
- Row
- BFD Interval
- The interval (in milliseconds) at which to send test packets to peers. The default is 300 ms, and you can enter a value from 3 to 30000 ms.
- Row
- BFD Multiplier
- The multiplier is the number of consecutive packets that can be lost before BFD considers a peer down and shuts down BGP. The default is 3, and you can enter a value from 2 to 16.
Session settings
These settings apply to all the prefixes you list below.
You can also set these on per-prefix basis. Settings specified on the prefix level override the session-level setting for that particular prefix.
You can leave these fields empty to accept the default values.
-
Header row
- Field
- Description
-
Row 1
-
AS Prepend
-
Number of additional times to add the ASN to the BGP path, resulting in a higher path length. Allowed values are integers from 0 to 5.
Routes with higher path length (a higher ASN prepend value) have a lower priority.
-
-
Row 1
-
MED
-
The multi-exit discriminator (MED) value. Allowed values are integers from 0 to 4294967295.
When the same route is advertised in multiple locations, those with a lower MED are preferred by the peer AS.
-
-
Row 1
- Local Preference
- When the same route is received in multiple locations, those with a higher local preference value are preferred by the PacketFabric Cloud Router. Allowed values are integers from 0 to 4294967295.
-
Row 1
-
Match type
-
This applies to all the allowed incoming and outgoing prefixes that you list below. You can also specify this on a per-prefix basis.
Exact means incoming or outgoing prefixes must be an exact match to the prefixes you specify. Or longer applies the
orlongermatch filter.For example, say you list
172.16.2.0/24as an allowed incoming prefix. You have three other cloud connections with the following outgoing prefixes:Connection A:
172.16.2.0/24
Connection B:172.16.0.0/16
Connection C:172.16.2.128/25If you select Exact, only routes from Connection A are allowed.
If you select Or longer, the routes from Connection A and Connection C are allowed. (Any IPs from 172.16.2.0/24 to 172.16.2.0/32 are allowed.)
-
-
Row 1
-
Network Address Translation
-
These options appear if you opted for NAT capability when creating the connection.
If you do not see these options or they are greyed out, your connection is not NAT capable.
Source NAT – Translate the source IP address. For example, you can translate a pool of private IP addresses to a public IP address in order to reach an external resource that only accepts public IPs.
Destination NAT – Translate the destination IP address. For example, if you need to translate a public IP address to a private IP addresses in your network. This may be necessary if you plan to make the connection exportable via Quick Connect.
-
Source NAT settings
- Row
- Field
- Description
- Row
-
Source NAT Direction
-
Egress: Egress SNAT. Traffic leaving the Cloud Router and entering your on-premises/cloud network will be subject to source NAT.
You would typically use this to translate private IP addresses to a public NAT pool as traffic exits your network. For example, 192.168.1.0/24 to 185.161.1.5/32.
Ingress: Ingress SNAT. Traffic leaving your on-premises/cloud network and entering the Cloud Router will be subject to source NAT.
You would typically use this to translate public IP addresses to a private NAT pool when directing traffic elsewhere in your network.
-
- Row
- Prefixes to NAT
- The prefixes from your on-premises environment that you want to associate with the NAT pool.
- Row
-
NAT Pool Prefixes
-
All prefixes that are NATed on this connection will be translated to the pool prefix address.
If this connection uses a PacketFabric-assigned public IP address, then this field should be pre-populated with a newly generated
/32public IP.If this connection uses a private IP address, then enter a
/32prefix that is different than the router peer IPs you entered above and not used on any of your other Cloud Router connections.
-
Destination NAT settings
- Row
- Field
- Description
- Row
- Pre-translation IP prefix
- The destination IP prefix that you want translated via DNAT.
- Row
- Post-translation IP prefix
- The destination IP prefix into which you want DNAT to translate your original (pre-translation) destination IP.
- Row
-
Conditional IP prefix
-
Optional. The prefix being received must fall within the conditional prefix range before the Cloud Router will advertise the pre-translation prefix.
Note that the post-translation prefix must be equal to or included within the conditional IP prefix.
-
Allowed prefixes to customer premises
This is a list of addresses that you want to allow into your on-premises router. These can be addresses from other cloud environments or from a different router. You can add up to 1000 prefixes.
The values you set above under Session settings apply to all prefixes. However, you can override those settings on a per-prefix basis.
For example, if you enabled Allow longer prefixes above but want to specify an exact prefix, then you can override the Allow longer setting by selecting Match type > Exact next to that particular prefix.
- Row
- Field
- Description
- Row
- Prefix/Mask
- Enter an allowed IP address range in CIDR format.
- Row
- Match type
- Allow or disallow longer prefixes for this row (see the description above).
- Row
-
AS prepend
-
Number of additional times to add the ASN to the BGP path, resulting in a higher path length. Allowed values are integers from 0 to 5.
Routes with higher path length (a higher ASN prepend value) have a lower priority.
-
- Row
-
MED
-
The multi-exit discriminator (MED) value. Allowed values are integers from 0 to 4294967295.
When the same route is advertised in multiple locations, those with a lower MED are preferred by the peer AS.
-
Allowed prefixes from customer premises
This is a list of addresses from within the on-premises environment that you want to advertise to other connections on the Cloud Router. You can add up to 1000 prefixes.
The values you set above under Session settings apply to all prefixes. However, you can override those settings on a per-prefix basis.
- Row
- Field
- Description
- Row
- Prefix/Mask
- Enter an allowed IP address range in CIDR format.
- Row
- Match type
- Allow or disallow longer prefixes for this row (see the description above).
- Row
- Local preference
- When the same route is received in multiple locations, those with a higher local preference value are preferred by the PacketFabric Cloud Router. Allowed values are integers from 0 to 4294967295.