Cloud Router NAT
The PacketFabric Cloud Router provides a network address translation (NAT) service.
NAT support overview
- Header
- Feature
- Supported
- Notes
- SNAT
- Egress Source NAT
-
- Many-to-one
- Achieved through NAT overload (NAPT)
- Dynamic NAT pool
- Currently there is no limit on how many prefixes you can have in the NAT pool
- SNAT
- Ingress Source NAT
- DNAT
- Egress Destination NAT
-
- Stateless NAT
- Currently limited to 20 mappings per connection.
- Static, with 1:1 mapping
- DNAT
- Ingress Destination NAT
- N/A
Limitations
- A connection can only support one type of NAT at a time.
- Connections with SNAT are limited to 2 Gbps each way.
- NAT is not currently supported for IPsec VPN connections
NAT-capable devices
Not all devices are NAT-capable. To ensure you build your Cloud Router connection on a device that supports NAT, use the NAT options when ordering that connection:
When configuring BGP for that connection, you can decide whether you want to actually configure NAT for the connection. There is no requirement to use it.
If you provision on a device that is not NAT-capable and later decide you want to use NAT, you will need to delete and rebuild that connection.
Cost
There is no additional cost for NAT connections.
Connection types
NAT is supported for all cloud service providers and for dedicated port connections.
It is not currently supported for IPsec VPN connections.
Public IPs for NAT
While the most common use case for NAT is to map private IP addresses to a public IP, you do not need to use a public IP address when implementing NAT.
- SNAT
- Most Cloud Router connections have the option to allocate a PacketFabric public IP address when provisioning the connection. The exceptions are IPsec connections and Google connections. You can also use your own public IP address.
- For these types of connections, we will auto-allocate a public IP address for your SNAT pool.
- DNAT
- We currently do not auto-allocate a public IP address for your DNAT pool. You will need to discuss this with your account manager or submit a technical support ticket. However, you can also use your own public IP address.
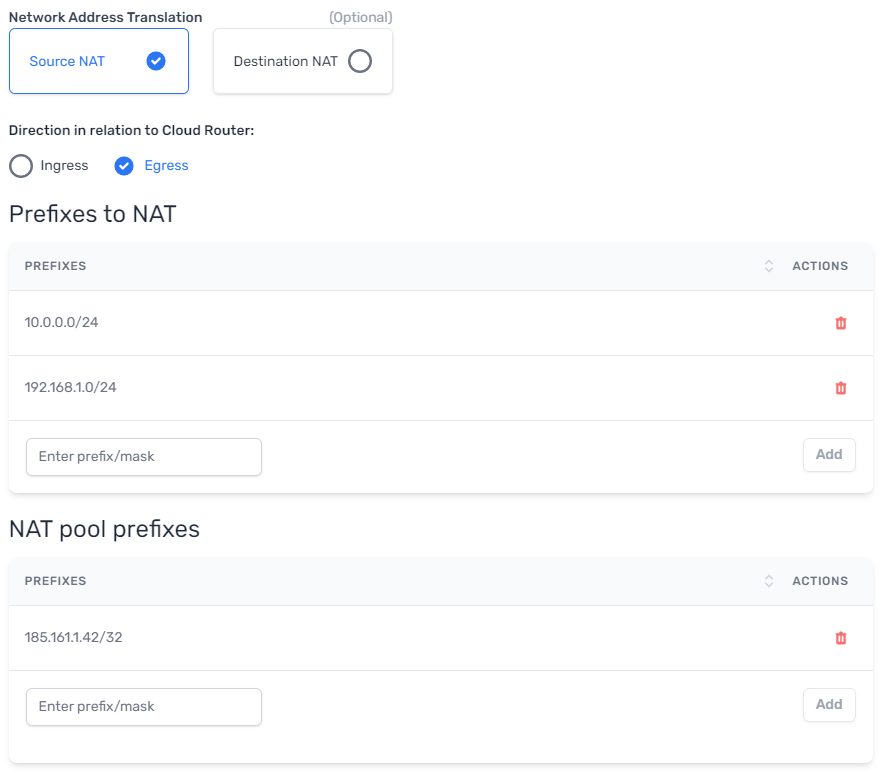
Source NAT
Source NAT (SNAT) translates the source IP address. You can use SNAT to allow your private resources to reach public networks or to communicate with overlapping networks.
We allow two types of SNAT: ingress and egress.
Egress SNAT
This is the most common NAT configuration.
Egress SNAT modifies the source IP address of a packet as it exits a network. This means that traffic leaving the Cloud Router and entering your on-premises or cloud network will be subject to source NAT.
You would typically use this to translate private IP addresses to a public IP address as traffic exits your network. This allows you to reach public cloud resources (such as AWS S3 and Microsoft 365) from a private cloud environment.
The example below is using NAT to connect Google Cloud to an AWS S3 bucket, and receiving various AWS public routes.
Ingress SNAT
Traffic leaving your on-premises/cloud network and entering the Cloud Router will be subject to source NAT.
You would typically use this to translate a pool of IP addresses to a single NAT address when directing traffic elsewhere in your network. This can provide easier IP address management when working between connections as well as allow you to reach public cloud resources via a public IP. Another common use case could be managing IP addressing conflicts during mergers or migrations.
Configuring SNAT
NAT configuration is available in the BGP Settings of a connection. You can configure, modify, and remove NAT at any time.
- Row
- Field
- Description
- Row
- Prefixes to NAT
- The prefixes from your on-premises environment that you want to associate with the NAT pool. Only the source IPs that fall into these subnests will be subject to source NAT.
- Row
-
NAT Pool Prefixes
-
All prefixes that are NATed on this connection will be translated to the pool prefix address.
If this connection uses a PacketFabric-assigned public IP address, then this field should be pre-populated with a newly generated
/32public IP.If this connection uses a private IP address, then enter a
/32prefix that is different from the router peer IPs you entered above and not used on any of your other Cloud Router connections.
-
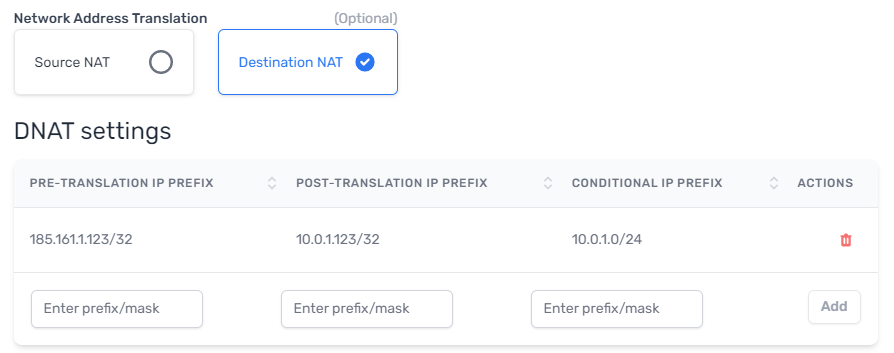
Destination NAT
Destination NAT (DNAT) translates the destination IP address.
Like SNAT, you can use DNAT to make private resources within your infrastructure reachable via a public IP address. DNAT allows you to publish services deployed internally with private or conflicting IP addresses, or to be exported to other Cloud Routers as unique public IPs.
In the example below, DNAT facilitates exportable routes that can be imported by other Cloud Routers.
In this example:
- Cloud Router 1 starts advertising 185.161.1.123/32.
- Every packet arriving at that Cloud Router with a destination IP of 185.161.1.123 will be modified and the destination IP will be substituted to 10.0.1.123.
- The packet will be routed to that destination based on the Cloud Router connection routing table entries.
- Every packet arriving through the DNAT enabled connection with the source IP of 10.0.1.123 will be modified to make the source IP 185.161.1.123.
- The packet will be routed according to the Cloud Router connection routing table.
Conditional prefix
The conditional IP prefix is optional. A conditional IP prefix enables failover behavior when you have redundant DNAT connections.
The presence of a conditional prefix means that whether the DNAT prefix is advertised depends on the presence of the conditional prefix in the Cloud Router connection routing table.
Without the conditional prefix specified, the Cloud Router starts advertising the pre-translation IP prefix (the public DNAT prefix in the example above) as soon as the configuration is applied, and will continue to do so until the configuration is removed. However, this creates a potential traffic black hole if the router does not have a route towards the post-translation IP prefix (the private IP address in the example above).
In other words, traffic will be attracted to the DNAT prefix, however because the router will not have a route, the packets will be dropped. This could be caused by a BGP session to the cloud provider that is not configured yet, that is improperly configured, or if the connection goes down for any reason.
The conditional prefix allows you to avoid the above situation. In order to benefit from this, you will need to provision redundant DNAT connections on unique devices.
With the conditional prefix specified and with redundancy in place, under normal conditions the traffic load is shared; different ingress devices will likely forward to different routers. However, in the event of a device or link failure, the affected router will stop receiving the conditional IP prefix from the cloud provider. The pre-translation IP prefix will be withdrawn from the Cloud Router, and as a result traffic will be forwarded to the remaining routing devices, with minimal disruption.
Configuring DNAT
NAT configuration is available in the BGP Settings of a connection. You can configure, modify, and remove NAT at any time.
- Row
- Field
- Description
- Row
- Pre-translation IP prefix
- The destination IP prefix that you want translated via DNAT.
- Row
- Post-translation IP prefix
- The destination IP prefix into which you want DNAT to translate your original (pre-translation) destination IP.
- Row
-
Conditional IP prefix
-
Optional. The prefix being received must fall within the conditional prefix range before the Cloud Router will advertise the pre-translation prefix.
Note that the post-translation prefix must be equal to or included within the conditional IP prefix.
-